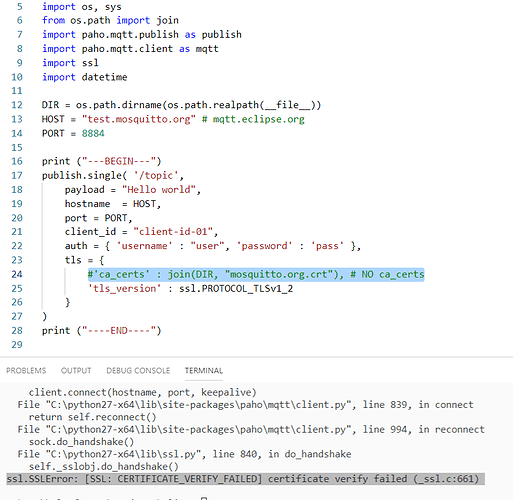
Hello,
I’m trying to verify server certificate in SSL connection on BG96. For some reason it works without certificate checking (seclevel 0), but doesn’t on higher seclevels. Here is example session:
AT
OK
ATI
Quectel
BG96
Revision: BG96MAR02A08M1G
OK
ATE1
OK
ATV1
OK
AT+QFLST
+QFLST: "ca-mq.pem",1078
+QFLST: "camq.pem",1078
OK
AT+QICSGP=1,1,"internet","","",0
OK
AT+QIACT=1
OK
AT+QIACT?
+QIACT: 1,1,1,"100.95.169.24"
OK
AT+QISTATE=0,1
OK
AT+QSSLCFG="seclevel",1,0
OK
AT+QSSLCFG="cacert",1,"camq.pem"
OK
AT+QSSLCFG="ciphersuite",1,0XFFFF
OK
AT+QSSLOPEN=1,1,4,"test.mosquitto.org",8883
OK
+QSSLOPEN: 4,0
AT+QSSLCLOSE=4
OK
AT+QSSLCFG="seclevel",1,1
OK
AT+QSSLOPEN=1,1,4,"test.mosquitto.org",8883
OK
+QSSLOPEN: 4,552
AT+QFDWL="camq.pem"
CONNECT
-----BEGIN CERTIFICATE-----
MIIC8DCCAlmgAwIBAgIJAOD63PlXjJi8MA0GCSqGSIb3DQEBBQUAMIGQMQswCQYD
VQQGEwJHQjEXMBUGA1UECAwOVW5pdGVkIEtpbmdkb20xDjAMBgNVBAcMBURlcmJ5
MRIwEAYDVQQKDAlNb3NxdWl0dG8xCzAJBgNVBAsMAkNBMRYwFAYDVQQDDA1tb3Nx
dWl0dG8ub3JnMR8wHQYJKoZIhvcNAQkBFhByb2dlckBhdGNob28ub3JnMB4XDTEy
MDYyOTIyMTE1OVoXDTIyMDYyNzIyMTE1OVowgZAxCzAJBgNVBAYTAkdCMRcwFQYD
VQQIDA5Vbml0ZWQgS2luZ2RvbTEOMAwGA1UEBwwFRGVyYnkxEjAQBgNVBAoMCU1v
c3F1aXR0bzELMAkGA1UECwwCQ0ExFjAUBgNVBAMMDW1vc3F1aXR0by5vcmcxHzAd
BgkqhkiG9w0BCQEWEHJvZ2VyQGF0Y2hvby5vcmcwgZ8wDQYJKoZIhvcNAQEBBQAD
gY0AMIGJAoGBAMYkLmX7SqOT/jJCZoQ1NWdCrr/pq47m3xxyXcI+FLEmwbE3R9vM
rE6sRbP2S89pfrCt7iuITXPKycpUcIU0mtcT1OqxGBV2lb6RaOT2gC5pxyGaFJ+h
A+GIbdYKO3JprPxSBoRponZJvDGEZuM3N7p3S/lRoi7G5wG5mvUmaE5RAgMBAAGj
UDBOMB0GA1UdDgQWBBTad2QneVztIPQzRRGj6ZHKqJTv5jAfBgNVHSMEGDAWgBTa
d2QneVztIPQzRRGj6ZHKqJTv5jAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBBQUA
A4GBAAqw1rK4NlRUCUBLhEFUQasjP7xfFqlVbE2cRy0Rs4o3KS0JwzQVBwG85xge
REyPOFdGdhBY2P1FNRy0MDr6xr+D2ZOwxs63dG1nnAnWZg7qwoLgpZ4fESPD3PkA
1ZgKJc2zbSQ9fCPxt2W3mdVav66c6fsb7els2W2Iz7gERJSX
-----END CERTIFICATE-----
+QFDWL: 1078,6e2f
OK
AT+QSSLCFG="sslversion",1,4
OK
AT+QSSLOPEN=1,1,4,"test.mosquitto.org",8883
OK
+QSSLOPEN: 4,552
AT+QSSLCFG="ignorelocaltime",1
+QSSLCFG: "ignorelocaltime",1,1
OK
AT+QSSLCFG="ignorelocaltime",1,0
OK
AT+QSSLCFG="ignorelocaltime",1
+QSSLCFG: "ignorelocaltime",1,0
OK
AT+QSSLOPEN=1,1,4,"test.mosquitto.org",8883
OK
+QSSLOPEN: 4,552