I’ve been using the BG96MA for a while now and every now and then I have problems with the commands AT+QHTTPPOST and AT+QHTTPPOSTFILE. With some combinations of firmware version, POST command, server and payload I always get an error 719 (HTTP socket closed). For example: I’ve been using firmware version BG96MAR02A07M1G_01.016.01.016 and the AT+QHTTPPOST command without a problem for months. But now I have modules with version BG96MAR03A06M1G_01.005.01.005 and the command practically always returns error 719. After using the AT+QHTTPPOSTFILE command, most of the connections work with the newer firmware, but modules with an older firmware now return error 719.
I managed to find a minimal example that shows the error with firmware versions BG96MAR02A07M1G_01.011.01.011 and BG96MAR03A06M1G_01.005.01.005. The error can be reproduced on custom hardware/firmware and on a BG96 Eval-Kit using QNavigator. If I use following commands one request succeeds, while the other fails. I omitted commands that deal with the connection to the GPRS network, since the connection obviously works. The only difference between both requests, is that one contains an authorization token and the other does not.
# Setup connection
>>> AT+CFUN=1
>>> AT+CGDCONT=1,"IPV4V6","TM"
>>> AT+COPS=0,0,"",0
>>> AT+QHTTPCFG="requestheader",1
>>> AT+QICSGP=1,1,"TM"
>>> AT+QIACT=1
# This request succeeds
>>> AT+QHTTPURL=24,120
>>> https://httpbin.org/post
>>> AT+QFDEL="HTTPPOST.TMP"
>>> AT+QFUPL="HTTPPOST.TMP",1554,120
### ... [Upload file HTTP_ok.TMP from bg96_error_719.zip]
>>> AT+QHTTPPOSTFILE="HTTPPOST.TMP",120
# This request fails
>>> AT+QHTTPURL=24,120
>>> https://httpbin.org/post
>>> AT+QFDEL="HTTPPOST.TMP"
>>> AT+QFUPL="HTTPPOST.TMP",2061,120
### ... [Upload file HTTP_fail.TMP from bg96_error_719.zip]
>>> AT+QHTTPPOSTFILE="HTTPPOST.TMP",120
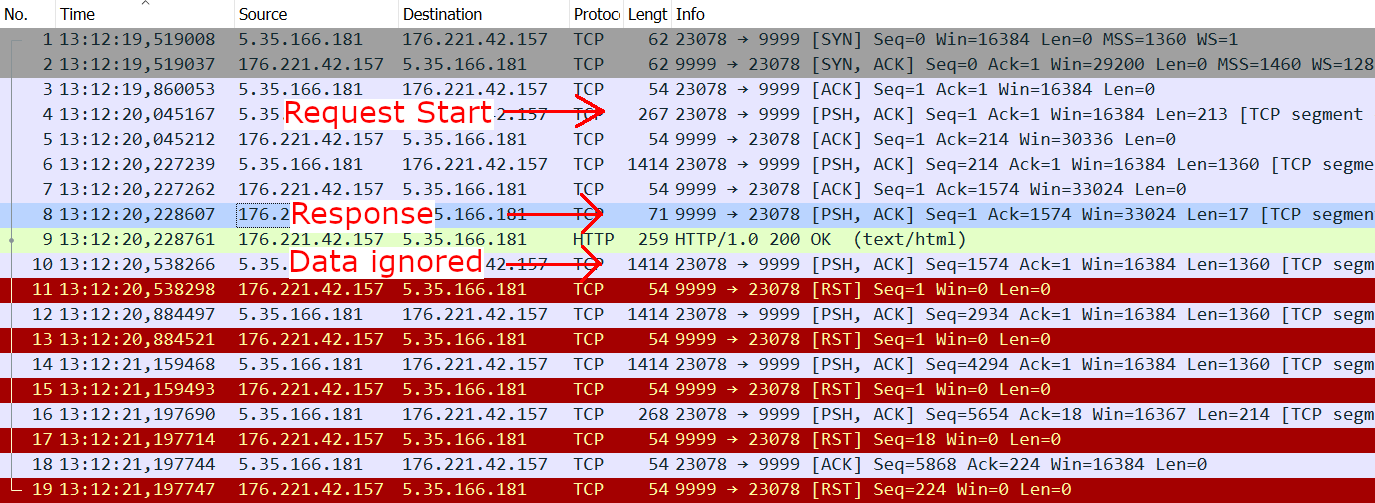
I tried POST requests with multiple HTTP servers (Apache, Flask, Gunicorn) and this error can be seen on any of them. When running a simple Flask server, it actually seems like all data is being received correctly and the server sends a correct HTTP response. But somehow this gets mixed up with the data being send. A Wireshark trace on the server shows, that the request and the response get mixed up and some of the data is rejected with a Reset-Flag (RST).
What exactly leads to this error and how can I fix my HTTP POST requests? The data to reproduce the error can be found in following zip file.
bg96_error_719_data.zip (3.2 KB)