Hi
I am trying to access the API
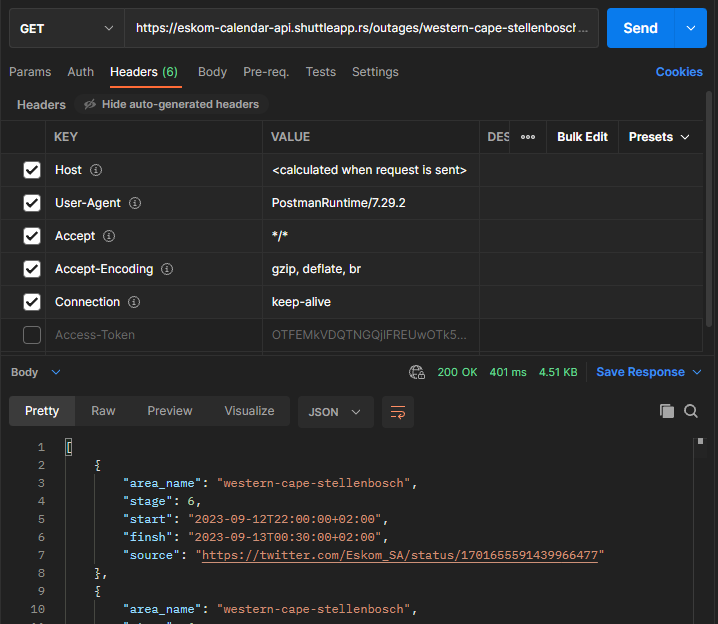
https://eskom-calendar-api.shuttleapp.rs/outages/western-cape-stellenbosch
(alternative method is curl https://eskom-calendar-api.shuttleapp.rs/outages/western-cape-stellenbosch | jq , or directly via browser)


T+QHTTPCFG="contextid",1
AT+QHTTPCFG="responseheader",1
AT+QHTTPCFG="contenttype",1
AT+QIACT?
AT+QICSGP=1,1,"internet","","",1
AT+QIACT=1
AT+QIACT?
AT+QHTTPCFG="sslctxid",1
AT+QSSLCFG="sslversion",1,1
AT+QSSLCFG="ciphersuite",1,0x0005
AT+QSSLCFG="seclevel",1,0
AT+QHTTPURL=74,80
https://eskom-calendar-api.shuttleapp.rs/outages/western-cape-stellenbosch
AT+QHTTPGETEX=60,1,256
response:
QIACT: 1,1,1,"100.95.188.189"
OK
OK
OK
OK
OK
CONNECT
OK
OK
+QHTTPGET: 732
Hi Pieter
When I tested GETEX according to your process, it still reported an error. Changing the module test on other platforms also had the same effect. However, using the POSTMAN tool, the entire package can be GET normally, which shows that there is no problem with RUL.
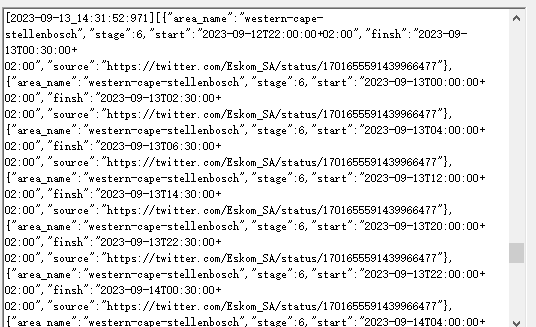
Then use the request header to request the data within the range, and still get the entire package of data, not the specified data download.
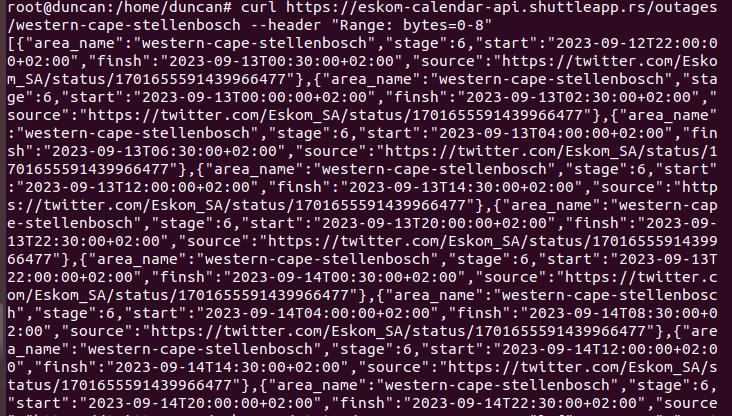
Using curl to verify on Ubuntu, the entire package of data is also obtained, but a piece of data cannot be obtained.
It is suspected that the server does not support obtaining the specified range of data. Please help confirm this problem. Thank you.
AT+QHTTPGET=80 also gives the same error - +QHTTPGET: 732
Getting all the informatiion is OK, I just need the information.
I tried with and without SSL config, and many other options.
thanks for the reply
I have tested the HTTPGET and the return same as you.
Maybe you can choose other server to test.
site uses
SSL-Session: - Protocol : TLSv1.3
EG915 only supports
SSL Versions
SSL 3.0
TLS 1.2
TLS 1.1
TLS 1.0
any firmware update available?
Currently, EG915N does not support TLS1.3. We will consider developing TLS1.3 in the future.